2.9
- Automating the creation of a honeypot
- Gerix
Wifi Cracker is a software tool designed to automate attacks against
Wi-Fi networks. Due to the fact that a Graphical User Guide (GUI) is
available, the easiness of use is improved in comparison with command
shell:
- For
starting Gerix from the "kali" command shell:
- Gerix
is launched:
- On
the Configuration tab, and selecting wlan0 interface, clicking
Enable/Disable Monitor Mode puts wlan0 in promiscuous/monitoring
mode:
- The
virtual interface mon0 is created. To change the MAC address, so that
it cannot be recognized, Set random MAC address tab is clicked:
- Now,
both mon0 and wlan0 have changed their MAC address numbers. It is
important to write down the MAC address 58:6D:BC:54:58:C9, because it
will be the MAC associated to the fake AP "honeypot":
- Clicking
the tab Fake AP, the honeypot is created without any authentication.
Of course, in a real environmente, an attacker would use a less
suspicious network name like "honeypot":
- Gerix
announces the creation of the honeypot. Actually, it can be checked
that the real command shell is airbase-ng, working behind the
Gerix GUI:
- Now,
"kali" detects its owned created fake AP, wich ESSID is
"honeypot", and MAC address 58:6D:BC:54:58:C9. So
far, no client is associated to "honeypot":
- From
"roch", Vistumbler detects "honeypot" with all
its features:
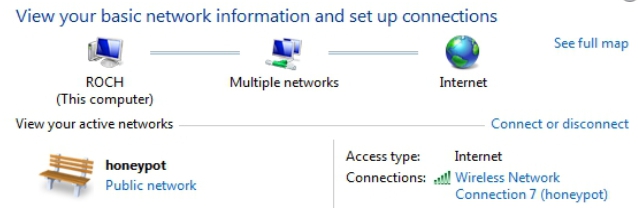
- Now,
it is time to connect the victim "roch" to the network:
- The
association is succesful:
- Gerix
announces that a client with MAC 28:C6:86:63:15:6B ("roch"s
MAC address) has associated to the network whose ESSID is "honeypot":
- Also,
airodump-ng detects "roch" connected to "honeypot":
- So,
the deception to the victim has been a success. The same attack could
have been done using another AP's legitimate name.