CRACKING AUTHENTICATION WITH BURP FOR NETGEAR ROUTER EMULATED FIRMWARE
- Layout for this exercise:

- This exercise is based in a previous emulation of Netgear firmware:

- Downloading the free edition of Burp Suite in its .JAR file version:
https://portswigger.net/burp/freedownload


- The .JAR file is downloaded:

- Launching the application:

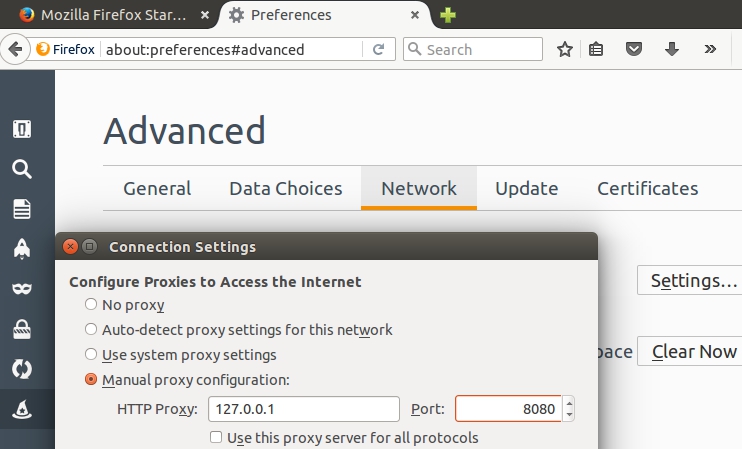
- After accepting all the default options for Burp, let's ensure that the proxy is listening locally (127.0.0.1) on port 8080:

- Also, let's configure Burp so that the interception applies for both the Client requests and the Server responses:

- Now, it is time to enable the proxy at the Firefox browser:
- Let's introduce some fake credentials, like for instance Username:Password

- Burp intercepts and displays the fake credentials:

- Looking into the tab "HTTP history", right clicking the request and choosing the option "Send to Intruder":

- The attack target is the known one (Firmware emulation with 192.168.0.100 and port 80):

- The attack consists on using two payload lists, the first one for the username and the second one for the password:

- Because this is a simple example, let's provide just 10 possible usernames and 10 possible passwords, totally 10x10 = 100 possible requests.
- For the username (list of 10):

- For the passwords (list of 10):

- As said before, in this simple case the total Request count is 100 (10x10):

- However, in a real scenario case, and using the Pro version of Burpsuite, large wordlist text files could be provided. Of course, trying many possible combinations would take a longer time to perform the attack:

- Starting the attack:

- It is noticeable that the only trial (number 3) with a status 200 OK and different length (313) corresponds to admin:password, what are the default credentials for the NetGear device, meaning that the attack is successful.
- Also, the 3th trial yields a loginok response message:

- It is interesting to notice that this attack has been launched against an "emulated firmware", and not against an actual physical device.