ROOTKIT DETECTION WITH RKHUNTER (ROOTKIT HUNTER)
- Layout for this exercise:

1 - Introduction
- A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or areas of its software that would not otherwise be allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software.
- The term rootkit is a concatenation of "root" (the traditional name of the privileged account on Unix-like operating systems) and the word "kit" (which refers to the software components that implement the tool). The term rootkit has negative connotations through its association with malware.
- In other words, rootkits are software secretly installed by a malicious intruder to allow that user continued access to the system once security is breached. This is an extremely dangerous problem, because even after the entry vector that the user originally used to gain access is fixed, they can continue to enter the system using the rootkit they installed.
- Rootkit installation can be automated, or an attacker can install it once they've obtained root or Administrator access. Obtaining this access is a result of direct attack on a system, i.e. exploiting a known vulnerability (such as privilege escalation) or a password (obtained by cracking or social engineering tactics like "phishing").
- Once installed, it becomes possible to hide the intrusion as well as to maintain privileged access. The key is the root or administrator access. Full control over a system means that existing software can be modified, including software that might otherwise be used to detect or circumvent it.
https://en.wikipedia.org/wiki/Rootkit
2 - Rookit detection with rkhunter (rootkit hunter)
- Rootkit detection is difficult because a rootkit may be able to subvert the software that is intended to find it. Detection methods include using an alternative and trusted operating system, behavioral-based methods, signature scanning, difference scanning, and memory dump analysis.
- Rootkit removal can be complicated or practically impossible, especially in cases where the rootkit resides in the kernel; reinstallation of the operating system may be the only available solution to the problem. When dealing with firmware rootkits, removal may require hardware replacement, or specialized equipment.
- One tool that can help protect the system from these kinds of problems is rkhunter (rootkit hunter) . This software checks the system against a database of known rootkits. Additionally, it can check other system files to make sure they are in line with expected properties and values.
- rkhunter is a Unix-based tool that scans for rootkits, backdoors and possible local exploits. It does this by comparing SHA-1 hashes of important files with known good ones in online databases, searching for default directories of rootkits, wrong permissions, hidden files, suspicious strings in kernel modules, and special tests for Linux and FreeBSD.
- rkhunter has been written in Bourne shell, to allow for portability. It can run on almost all UNIX-derived systems.
https://en.wikipedia.org/wiki/Rkhunter
3 - Installing and updating rkhunter
- rkhunter can be downloaded from here:
http://rkhunter.sourceforge.net/
https://sourceforge.net/projects/rkhunter/

- Downloading the last version:


- Uncompressing (z), extracting (x), verbose (v), archive file (f), a new directory is created:

- Installing options help:

- Installing:

- Updating database files that contain information that rkhunter checks against to determine if a file or behavior is suspicious or not:

- Updating current configuration files values:

4 - Running rkhunter
- Now that everything is properly installed and updated let's run the program with option -c.
- First, rkhunter checks for system commads:
- Also, a long list of rootkits is checked against the database:
- Checking the network:

- Checking the local host:
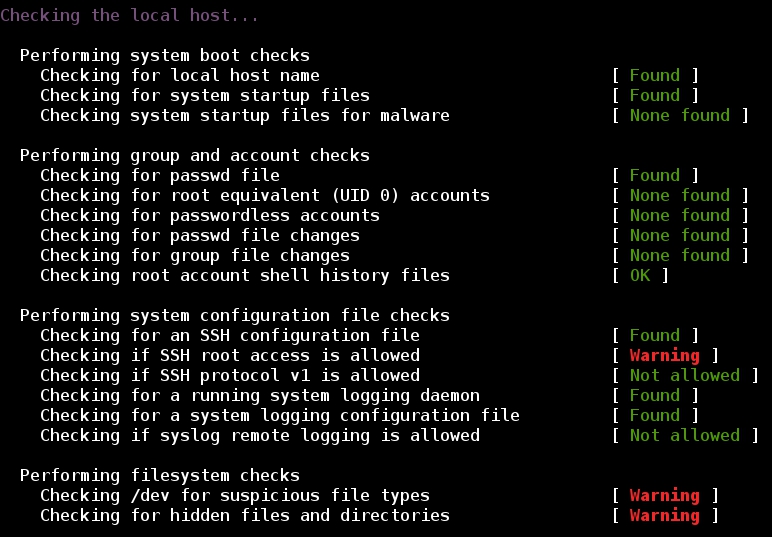
- Summary:

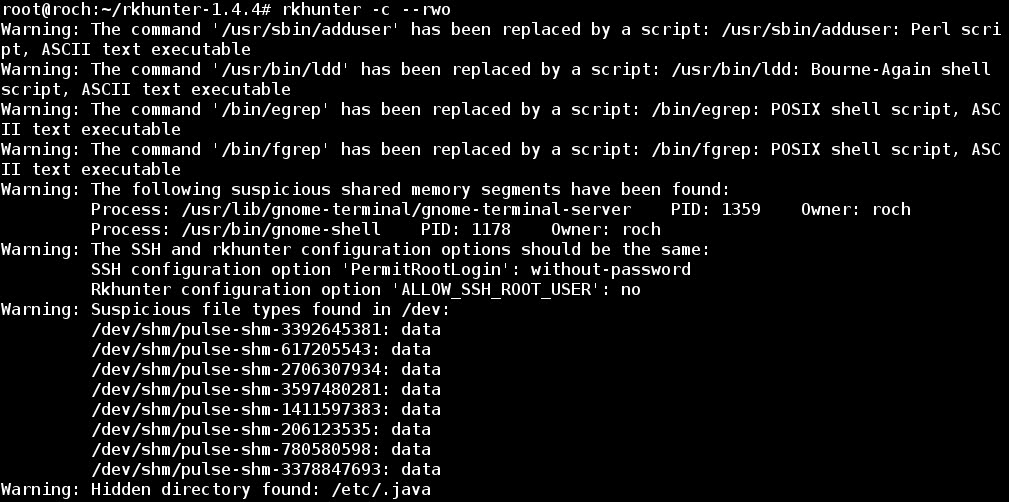
5 - Searching for warnings to be fixed
- As seen at previous picture all results have been sent to the var/log/rkhunter.log file. The oputput of the log is huge:
--- etc ---
- So, grepping for just warnings:

- From all the warnings issued we will try to fix the following two:
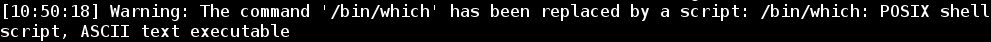
a) warning about the executable command /bin/which being replaced by a script:
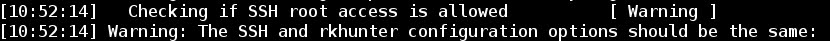
b) warning of different configurations about SSH root access:
- Fixing these warnings will prevent those files from triggering false positives on all subsequent checks.
6 - Warning about replacement of command /bin/which
- The command /bin/which is used to find the location of a program and it is part of the package debianutils (provides a number of small utilities which are used primarily by the installation scripts of Debian packages):
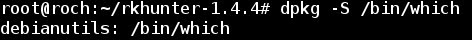

- To allow /bin/which as a script file it can be included into the SCRIPTWHITELIST list, just editing /etc/rkhunter.conf:


- Updating the files:
- Running again rkhunter, now with the option -rwo (report warnings only):
- As expected, warnings about /bin/which have disappeared.
7 - SSH root access warning
- Now, let's fix the warning about SSH root user access permissions:

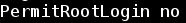
- Let's change the SSH configuration, setting to "no" the PermitRootLogin directive:

- Replacing "without-password" with "no":
- Restarting SSH service:
- Updating rkhunter files:
- Running again, now there is no warning about SSH root access:

8 - Scheduling database update with crontab
- Editing crontab with nano editor:

- Scheduling update for everyday at 0:00 and sending notification to a log file:

- By the way, notification of the warnings can be sent by email just editing /etc/rkhunter.conf:

