ANTIVIRUS EVASION / Veil Framework (I): Installation and setup
- Layout for this exercise:

1 - Introduction to Veil Framework
- The Veil Framework is a collection of security tools that implement various attack methods focused on evading antivirus detection.
https://www.veil-framework.com/framework/
https://github.com/Veil-Framework
- The most recent version at this moment (Veil 3.1.4) is composed of these tools:
a) Evasion generates payload executables that bypass common antivirus solutions.
b) Ordnance quickly generates Metasploit stager shellcode.

2 - Installing Veil Framework
- In this exercise we are using a Kali Linux distribution.
- In case git is not installed:
- From Veil github, copying to the clipboard:
- Cloning:
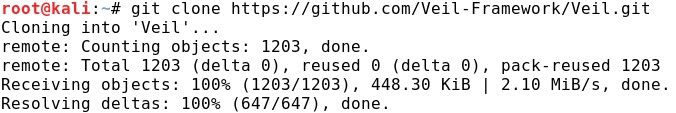
- A new directory Veil is created:

- Setting up the framework:

3 - Browsing Veil Framework options
- Launching the program:

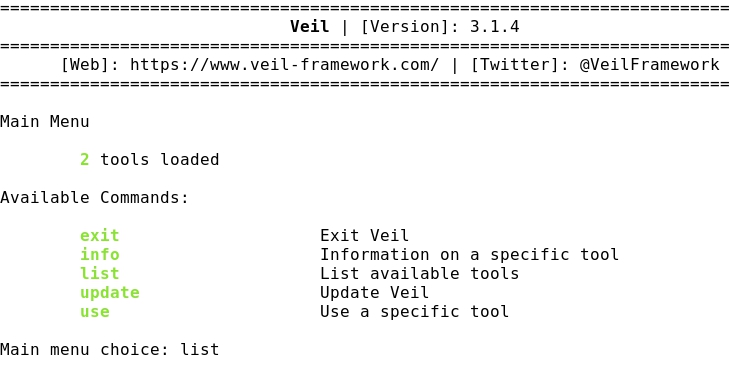
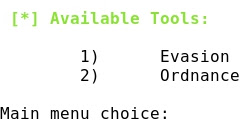
- Veil provides some commands. For instance the command list displays the two available tools, Evasion and Ordnance:
4 - Evasion
- Choosing Evasion:
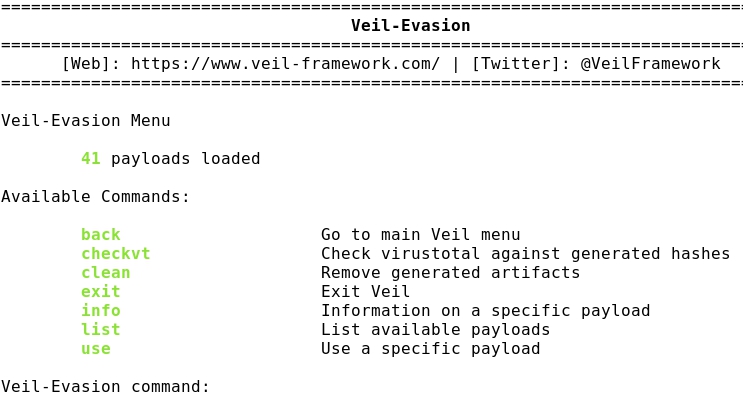
- Listing the 41 Evasion payloads:
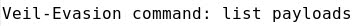
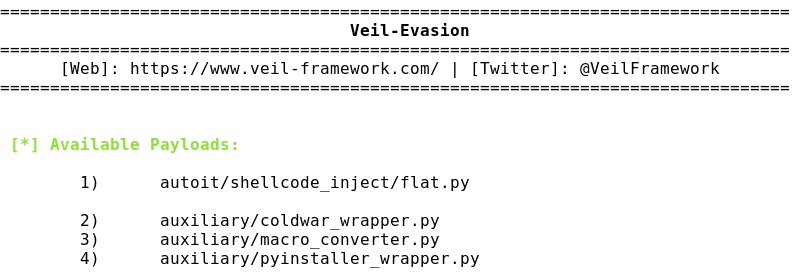
......................... etc ............................................................
5 - Ordnance
- Choosing Ordnance:
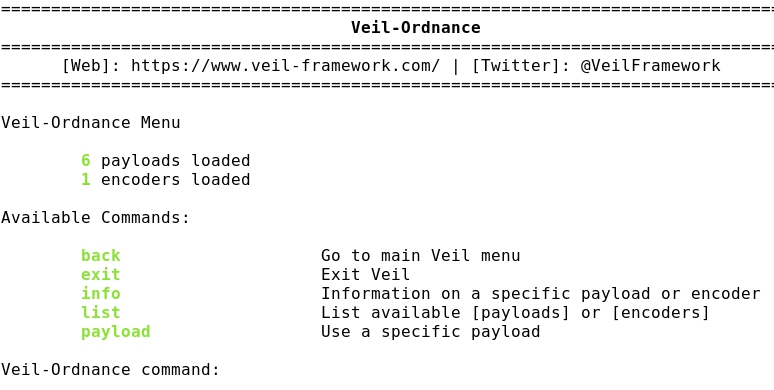
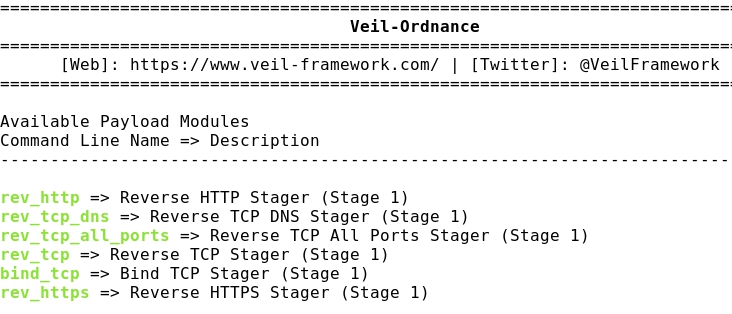
- Listing Ordnance payloads:
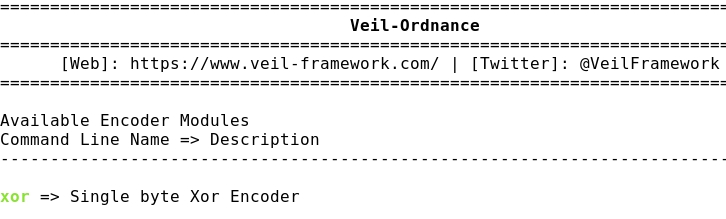
- Listing Ordnance encoder (XOR):