LORD OF THE ROOT 1.0.1
- Layout for this exercise:

1 - INTRODUCTION
- The goal of this exercise is to develop a hacking process for the vulnerable machine Lord Of The Root:
- Lord Of The Root can be downloaded from here:
- Once downloaded and extracted with VirtualBox:

2 - ENUMERATION
- Discovering the IP with netdiscover:

- Scanning with Nmap:

- Connecting with SSH there is message about Knock 1,2,3:

- Nmap helps to unknock ports 1,2,3 by using these options:
- -r: Scan ports consecutively - don't randomize
- -Pn: Treat all hosts as online -- skip host discovery

- A new open port 1337 is discovered, where an Apache web server is running:

- Dirbusting, the folder /images is found:

- Going to folder /images:

- Clicking the 3 images:



- Nothing of particular interested is found, even using strings or viewsourcing the page.
- However, when using ViewSource over robots.txt an encoded string is found:

- Viewing the source of /robots.txt:

- Decoding the Base64 string:

- Decoding again we find a reference to the folder /978345210/index.php:

- Going to /978345210/index.php there is a login form:

3 - SQL INJECTION
- Let's use SQLMAP to perform automated Sql injections.
- First, discovering the existing 4 databases:

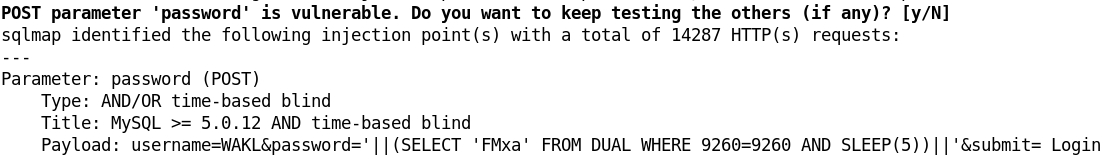

- Focusing on mysql, let's find tables, columns and credentials:


- We stop the injection once User and Password columns are detected:


- Credentials for root are found:



- Changing to database Webapp and following similar procedures than with previous database:






- Finally we have found credentiales for these 6 users: root, frodo, smeagol, aragorn, legolas, gimli.
4 - GETTING A REMOTE SHELL
- Let's use Hydra to attack the SSH server:



- So the only user that allows the SSH connection is smeagol, which password is MyPreciousR00t:

- Unfortunately smeagol is not a sudoer:

5 - PRIVILEGE ESCALATION
- Let's try 2 ways of Privilege Escalation:
5.1 - Buffer Overflow Exploitation
- Before starting the BOF exploitation let's check that ASLR is enabled, and unfortunately it is not possible for smeagol to disable this security measure:

- The folder SECRET contains 3 folders:

- Inside those folders there are 3 files that are owned by root and have the SUID bit set, what make them interesting to be exploited:

- The 3 files are executable, 2 of them seem to be identical according to their same SHA1 hashes, while the other is different:

- Running the 3 files without arguments the result is that an <input string> is required:



-However, after around 5 minutes the content of door1, door2 and door3 is switched:

- Before another switch happens let's transfer the file that is different to /tmp, so that we can study it calmly, without switching interruptions:


- Let's try how file works, for instance entering a short string:

- However a Segmentation fault is detected when the input is a long string:

- To begin the BOF exploitation let's create a 1000 characters long pattern:

- Starting GDB and passing the pattern to file:

- There is a Segmentation fault and the EIP is overwritten with 0x41376641 whose offset from the beginning of the pattern is 171:


- Running the next script, the EIP is now overwritten with BBBB (0x42424242), meaning that we have control over the EIP:

- Checking registers:

- The ESP points to 0xbffff580:

- Now, let's add to the exploit the address pointed by ESP (reversely written in little endian form), a bunch of NOP characters \x90, and this well-known shellcode:
http://shell-storm.org/shellcode/files/shellcode-827.php
- Running the exploit a shell is spwaned successfully:

- This exploit works in the GDB environment because the ASLR is disabled, however it won't work in the real scenario of the folder /SECRET where ASLR is actually enabled.
- One way to bypass ASLR is bruteforcing the stack by writing an automated looped script that tries the exploit 2000 times, in the hope that one of these trials hits the EIP successfully and a shell is achieved:

.................................
- Finally, after a lot of trials a root shell is achieved:

- Though the uid is not set to root but yes the euid:

- Another way of neutralizing ASLR would be to use the ulimit -s unlimited comand, as explained here:
https://lore.kernel.org/patchwork/patch/658246/
https://www.exploit-db.com/exploits/39669

- This is possible because LordOfTheRoot is a 32 bits machine:

5.2 - Exploiting the kernel
- Checking the kernel and Ubuntu version:

- For this kernel there is a potential 'overlayfs' Local Privilege Escalation exploit:

- Downloading the 39166.c exploit:

- Setting an HTTP server on port 8000:

- Transferring the exploit from Kali to the /tmp folder of the victim:

- Compling, setting execution permissions and running the exploit, eventually we've got a remote root shell:

6 - CAPTURING THE FLAG
- Going to the /root folder we can read the Flag.txt:

